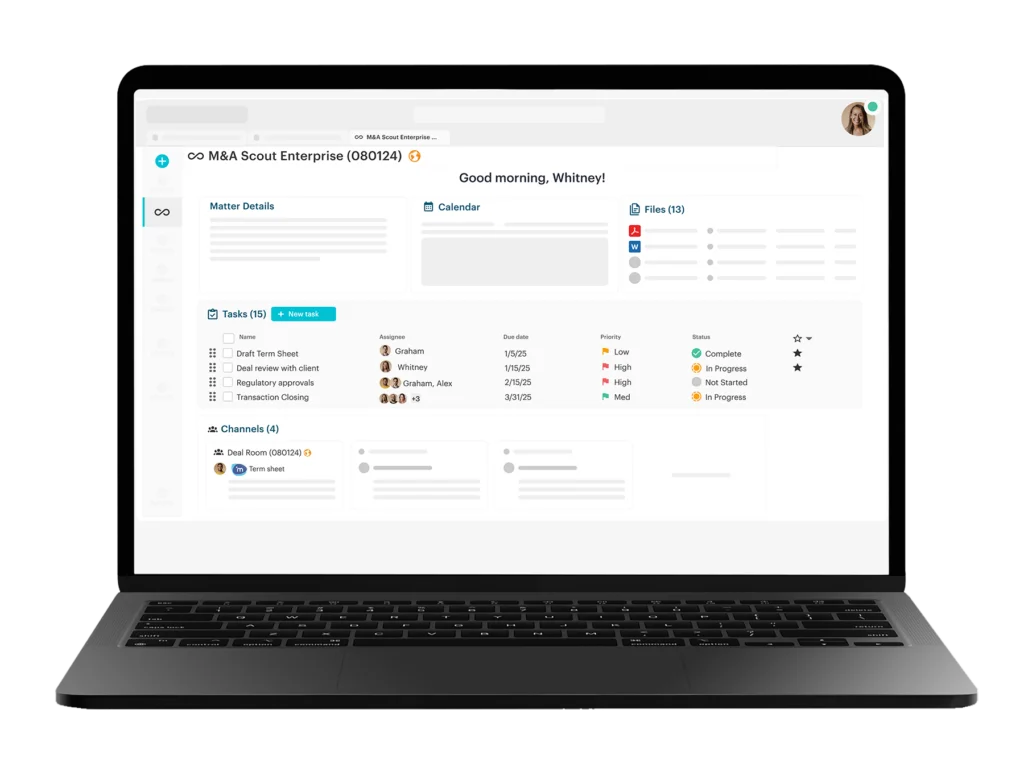
Earlier this summer, Workstorm was unveiled as the next-gen platform for enterprise collaboration. Designed for organizations that put serious business above all else, Workstorm is an all-in-one platform that enables businesses to collaborate securely, efficiently and seamlessly.
But, collaboration isn’t just about sharing ideas and documents. It’s about keeping those ideas and documents secure and confidential. It’s about data security.
Data Security is Workstorm’s Priority.
At Workstorm, the security of your data is the core focus of our technology and our business. We believe that your data is your data, not ours. These fundamental principles guide our decisions when it comes to infrastructure, software design, access rights and policy development. Let’s take a brief glimpse into each of these important security pillars.
- Infrastructure: Workstorm’s environment is constructed to ensure that you have the highest confidence in our safekeeping of your data. That means from the hosting deployment model and disaster recovery protocol, to monitoring controls and penetration tests, we are dedicated to ongoing identification, analysis and management of security risks relevant to our platform and your data.
- Software: Workstorm runs on a technology platform that is conceived, designed and built to operate securely. We uphold a software development and maintenance process that is critical to the availability and integrity of the Workstorm platform. Furthermore, our software enforces strong password creation requirements and has robust account administration.
- People: With background checks, confidentiality agreements and physical access controls, security is ingrained in our company’s culture and our employment practices. Workstorm employees understand the importance of protecting the information you entrust to us.
- Procedures: From compliance to data retention, Workstorm implements policies and procedures so that you can rely on our products to operate with the highest levels of security. Every decision we make involves answering questions about how a new feature or process impacts your security and privacy.